Via @torproject comes a link to a China Digital Times (a site run at Berkeley) that gives just a brief notice that some users behind the GFW are having their gmail login attempts redirected to hxxp://124.117.227.201/web/gmail/ where they are asked to enter their password. Chinese users reporting this redirect believe that the redirects are being performed by the ISP. Interestingly, 124.117.227.201 is a CNC host in Xinjiang.
At the time of this post the hxxp://124.117.227.201/web/gmail/ site is not operating (from the US or the PRC according to webpulse).
The original info apparently came from ntdtv:
中国ISP騙取gmail密码 被現場抓獲
UPDATE: I was looking closely at the screen cap that shows the source and it appears that part of the phishing app is hosted on ndns01.com, which doesn’t presently have an IP address assigned although the DNS record was updated on August 10.
This was an old news about ISP level Gmail phishing. More recently in June this year, Google warned that hackers were launching targeted phishing attacks against hundreds of Gmail account users, including senior U.S. government officials, Chinese political activists, military personnel and journalists. That story, as related in a post on the Official Google Blog, was retold in hundreds of media outlets today as the latest example of Chinese cyber espionage: The lead story in the print edition of The Wall Street Journal today was, “Google: China Hacked Email.”
The fact that hackers are launching extremely sophisticated email attacks that appear to trace back to China makes for great headlines, but it isn’t exactly news. I’m surprised by how few media outlets took the time to explain the mechanics behind these targeted attacks, because they offer valuable insight into why people who really ought to know better keep falling for them. A more complete accounting of the attacks may give regular Internet users a better sense of the caliber of scams that are likely to target them somewhere down the road.
Google said “the goal of this effort seems to have been to monitor the contents of targeted users’ emails, with the perpetrators apparently using stolen passwords to change peoples’ forwarding and delegation settings. (Gmail enables you to forward your emails automatically, as well as grant others access to your account.)”
This statement freaked me out a little bit. When was the last time you checked whether your email forwarding settings had been modified? If you’re like me, probably never. This might be the most useful aspect of the Google disclosure, and it contains a few helpful pointers about how to check those settings in Gmail. Google also took this opportunity to remind users about the value of enabling 2-step verification.
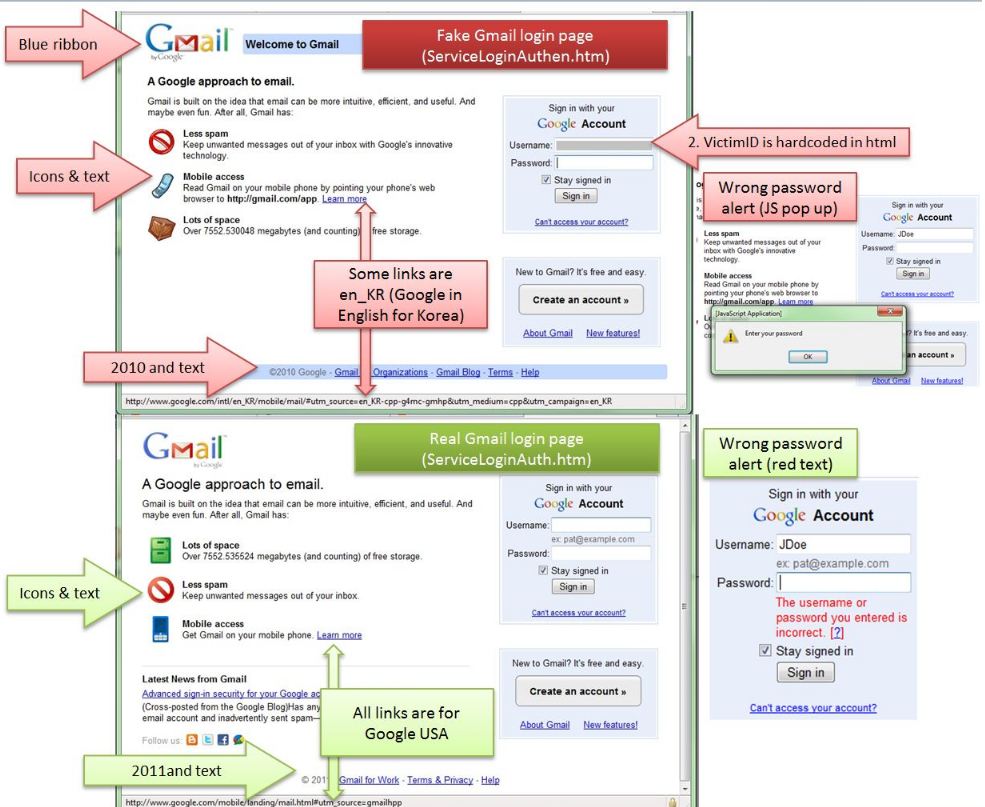
Most of targeted email attacks chronicled on Parkour’s blog involve poisoned file attachments that exploit zero-day software flaws in programs like Adobe Flash or Microsoft Word. This campaign also encouraged people to click a link to download a file, but the file was instead an HTML page that mimicked Gmail’s login page. The scam page also was custom-coded to fill in the target’s Gmail username. Contagiodump has a proof-of-concept page available at this link that shows the exact attack, except populated with “JDoe” in the username field.
Parkour also published an informative graphic highlighting the differences between the fake Google login page and the legitimate page at https://mail.google.com.
Some readers may think they’re not important enough to warrant targeted phishing attacks such as these, but the truth is that such phishing attacks can be automated quite easily. I’d be willing to bet that it won’t be long before more traditional, financially-motivated cyber crooks start incorporating these techniques in their scam emails.
Here are a few simple tips that can help you avoid becoming the next victim of these attack methods:
- Keep your software up-to-date. Legitimate, high-traffic Web sites get hacked all the time and seeded with exploit kits. Take advantage of programs like Secunia’s Personal Software Inspector or Filehippo’s Update Checker to stay abreast of the latest security updates.
- Be extremely judicious about clicking links in emails. Try to avoid responding to invites by clicking links in emails. I notice that Twitter has now started sending emails when someone re-tweets your posts: Avoid clicking on those as well. It’s safest to manage these accounts by visiting the sites manually, preferably using a bookmark as opposed to typing these site names into a browser address bar.
- Pay close attention to what’s in the address bar: Checking this area can prevent many email-based attacks. Staying vigilant here can also block far more stealthy attacks, such as tabnabbing.
- Consider using an email client, such as Mozilla’s Thunderbird, to handle your messages. It’s a good idea to have emails displayed in plain text instead of allowing HTML code to be displayed in emails by default.



In this situation, users are always vulnerable to be attacked if they continue to use the Domain Server from that illegal ISP.
Even an experienced user cannot be that careful all the time. I mean if you are in The Matrix, you will never win The Matrix, right? Unless you are Neo. 🙂
To avoid the domain hijacking and phishing, one has to either change the domain server or use the Google’s 2-step verification.
I’m surprised that so many Gmail accounts could be hacked so as to provide access to this particular scam.
As I understand it, these phishing attachments are sent from hacked accounts to colleagues who in turn open the attachments which prompts them to re-enter account info, thereby perpetuating the scam.
Well one thing is a malicious link in an e-mail that takes you to a scam site. Experienced users are not likely to click those and even if they click, they can see that something is wrong. Less experienced users can obviously fall for it.
Another thing is the ISP redirecting you to a malicious site. There, all bets are off. If I type gmail.com in the address bar or click it in my favorites, I’m just going to assume I’m actually at Gmail…
One thing that I didn’t think was clear here: were the attackers serving the page over HTTP or HTTPS? Next, what does it mean by “have their login attempts redirected?” Does that mean that the ISP was injecting a malicious link on the Google home page, or that they were actually capturing HTTP requests to mail.google.com and returning an HTTP Redirect 302 or something to the other website?
I think they served the page over HTTP. Concerning”have their login attempts redirected”,we can recall the presentation of ” Internet Censorship in China: Where Does the Filtering Occur? ” by Joe. The filtering server captures the request with sensitive information and disconnects the user from the target website. In this case, the filtering server captures the HTTP requests to mail.google.com and returns an HTTP Redirect to 124.117.227.201/web/gmail/.